
Software DevelopmentVCAA Exam Post Mortem2007
|
||||||||||||||||||||||||||||||||||||||
Post Mortem Notes This is not a VCAA publication.
I do not speak for the VCAA, the IT examiners, or exam markers. I was not involved in the writing or marking of this examination. Extracts from exams are all Copyright © VCAA, and are used with permission. Use these post mortems at your own risk. I reserve the right to change my mind completely, at short notice, about anything I've said here. Suggestions, discussions and corrections are welcome. Questions look like this. |
||||||||||||||||||||||||||||||||||||||
|
Other VCE IT Exam Post Mortems to enjoy IPM / ITA / Informatics / Data Analytics - 2001 | 2002 | 2003 | 2004 | 2005 | 2006 | 2007 | 2008 | 2009 | 2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2023
|
||||||||||||||||||||||||||||||||||||||
State averages added 26 Feb 08 | ||||||||||||||||||||||||||||||||||||||
Section AMultiple Choice |
||||||||||||||||||||||||||||||||||||||
Question 1 A. GSX Super Notebook B. HSV Games Notebook C. SP Business Notebook D.* GTX Student Notebook Easy peasy. 94% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 2 A. designing, testing, operating. The SDLC's steps are ADDIE according to the VCAA. The Software development cycle is ADDTDIE. The Problem Solving Methodology used in ITA has ADDTDIE. Anyone know the difference between them? Anyone at all? 71% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 3 A. arrays can only store the same type of data in each element.* It's true. 50% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 4 A. view and edit program icons. Most languages now have an editor bundled in with the compiler and linker and debugger to form an Integrated Development Environment or IDE. I believe the first to do this was Turbo Pascal way back when. 56% of the state got this right.
|
||||||||||||||||||||||||||||||||||||||
Question 5 A. stability, reliability and usability.* Popularity is not always important. Sustainability is not as important as any of the items in A. 75% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
The following diagram shows the folder structure for a file server. Use this diagram to answer Questions 6 and 7. |
||||||||||||||||||||||||||||||||||||||
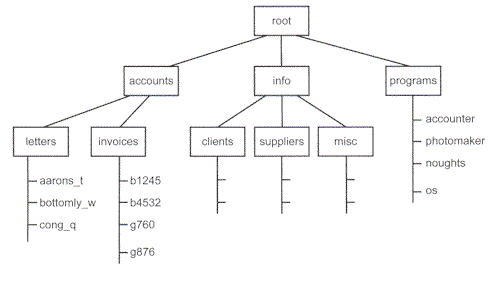 |
||||||||||||||||||||||||||||||||||||||
Question 6 A. a file. A bit easy, I thought. 84% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 7 A. invoices\b4532 The others are just silly. 65% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 8 A. floating point. Hmmm. Far too easy for clever-clogs doing SD. 54% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
The following information is to be used to answer Questions 9, 10 and 11. Programs A, B and C were run 1000 times each on the same computer. The following statistics were
|
||||||||||||||||||||||||||||||||||||||
Question 9 A. Program A is more efficient than Program C.* A couple of bits of knowledge are needed for this:
B is more efficient than A (2.9<3.2). C is the least efficient at 3.5 seconds' executing speed. A and C are both less efficient (slower) than B. 55% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 10 A. Program A is more reliable than Program C. Were you looking in the "Number of errors" line, children? Good! The lower the number, the more reliable it was. 70% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 11 A. Program B is an unstable program. Look at the number of crashes. 72% of the state got this right.
|
||||||||||||||||||||||||||||||||||||||
Question 12 IF b > 10 AND b < 20 THEN The best set of test data for b to test this algorithm is A. 10, 11, 15, 19,20 Good test data checks valid and invalid values and boundary conditions - the point at which the behaviour of the software should change. Printing of b will happen for numbers 11 to 19 inclusive. You would want to test that 10 and 20 are not erronously included. You want a typical in-range value (e.g. 12). Option C has all those features. 71% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 13 A. the analysis phase Note that this all took place after system implementation, so it can't be analysis or testing. 'Operational' doesn't exist. Evaluation is when system performance is reflected on. 79% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 14
This data would show that the objective has been met if the objective was A. a success rate of less than 4% What a strange question. What was it getting at, I wonder? 86% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 15 A. any program that runs on your computer to detect spies Well, duh. When in doubt, go for the option with the most words :-) 90% of the state got this right.
|
||||||||||||||||||||||||||||||||||||||
Question 16 A. bits per second. For D, I reckon the examiner ran out of convincing ideas for dud answers. hehehehe 83% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 17
Which statement about diagrams 1, 2 and 3 is true? A. The algorithm represented by diagram 1 is the same as that represented by diagram 2. Interesting approach to this topic. Nice question. I liked it a lot. The "not eof" decision was counter-intuitive, though - it's like a double-negative. Normally you test for EOF, not the opposite! Oh - by the way - EOF stands for "End of File". 60% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 18 A. data transfer rate over the network. Is it just me or is this a ridiculously easy question? 81% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 19 A. pilot conversion.* Straight-forward. Remember that pilot and parallel are not complete implementation methods. By themselves, they will not introduce the new system. They are optional accessories to the real, complete methods : direct and phased. 74% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Question 20 A. server technical manual, operating system manual, applications manual Hmmm. Notice the word "install" is bold and virtually has neon lights flashing the message, You don't really need applications on the server, so rub out A. System recovery manual? Not really. Networking and running the OS seems reasonable. Backup and recovery - what?? I'd say C. And if you're not enjoying the spectactular blinking of the "LOOK AT ME" message above, get Firefox! 57% of the state got this right. |
||||||||||||||||||||||||||||||||||||||
Section BShort Answer |
||||||||||||||||||||||||||||||||||||||
Question 1 Bus is based on a single backbone cable from which branch nodes. A break anywhere in the bus causes failure of the segment. It is usually found in old coaxial-cable networks. Star has a central distribution device, usually a switch, from which cables radiate to nodes. Hybrid is simply a combination of more than 1 topology, such as bus and star combined - often called a tree topology. • Bus: All nodes connecting computers and other devices are on the same cable (backbone). If one node fails everything after that will not work. |
||||||||||||||||||||||||||||||||||||||
Question 2 a. If he saves pictures on 300 days a year, how much storage space (in Gigabytes) will one year's images 60G 200M per day times 300 days = 60,000M = 60G , or It was pleasing that the majority of students answered this question correctly. A question such as this has not appeared on the paper in a number of years so it was reassuring that students could attempt the calculation correctly using the information provided. A number of students provided lengthy calculations, which was not required. Judy suggests that he burns the images onto CDs and then removes these images from his hard disk. The OCR program I used said he "bums the images" instead of "burns the images". Naughty, bad OCR! b. Describe one problem that Robert may have using CDs as his only photo storage solution. 2 marks. 6 lines. State average=1.5
Students needed to describe a problem that may occur if only CDs are used as a storage solution. For example, using CDs as the only storage solution is high risk, because if a CD was lost there would be no back up. In addition, Robert would need an excessive number of CDs to store all the images, and locating a file would be difficult. A majority of students were able to provide an appropriate response to this question. Those who did not receive full marks had generally misread the question. c. Describe and justify a better solution for Robert to use to store his pictures and keep them safe. 3 marks. State average=1.7 Solution: He'd want at least 2 copies of the pictures, preferably on different media types. A large (terabyte-sized) external USB hard disk plus identical copies on DVDs (which share some of the problems of CDs, but have much greater capacity.) If the exam book does not offer "prompts" for multi-part questions (1. Describe, 2. Justify), you can use your own subheadings to make it clear what you are talking about. It also reminds you to discuss each part! As this question was asking students to describe an appropriate storage/backup strategy, they needed to describe and justify a number of steps when formulating a strategy. For example, use two different media, such as DVD and an external hard disk, as they are relatively cheap and have a higher capacity then CDs. Store backups in different locations to the ensure safety of the original pictures. This question was poorly done. Many students did not pick up the key point that Robert had only one storage solution, which meant that they needed to provide two alternative storage media as a key part of their response. |
||||||||||||||||||||||||||||||||||||||
Question 3
A bit simple, if you ask me. Unless I've missed something.
Only 21 per cent of students gained full marks on this question as many students were unable to provide an appropriate ‘testing procedure’. Some students did indicate a test but then failed to describe what data they were looking for or what information they would gain from the test. For example, for the first criterion, ‘log server failures’ was an insufficient answer as it did not go on to state that this would need to be done over a period of time, that the log would need to be checked to ensure that there were fewer than two failures a month during that period, or that one month of testing would be insufficient to ascertain whether the criterion had been meet. |
||||||||||||||||||||||||||||||||||||||
Question 4
Hungarian notation was invented by Charles Simonyi, who programmed at Xerox PARC (which developed the mouse, GUI and Ethernet amongst other groundbreaking technology) and who later became Chief Architect at Microsoft. He is from Hungary, where - like in Japan - people's surnames precede their given name. He would have been called Simonyi Charles at home. Using appropriate naming conventions for variables and objects: |
||||||||||||||||||||||||||||||||||||||
Question 5 Since Mick produced the system as part of his work, rather than in his own time, the intellectual property rights would belong to his employer since it was "work product" according to the Copyright Act, 1968. If BN College were a government school, the education department would own the rights to the system. If BN College were independent, the college would own the rights to the system. But morally, Mick might claim ownership since he had created it with his own intellectual powers. Therefore, the government or college could probably legally restrict Mick's use of the system elsewhere, but ethically he could make a good case that the system was his 'baby' and only he had the copyright, especially if he came up with the idea on his own and worked on it out of work time, and let the college use it out of goodwill. It's a murky issue, and would make many lawyers a lot of money. But you can see the employer's point of view. If you are a games software company and hire a programmer to create a ripper game which earns millions - who should profit from the sales? The programmer, who was paid, or the company who hired him, paid him, and equipped him to do the job? Ah, this was interesting, and challenging. Probably too challenging from a legal point of view. From http://www.copyright.org.au/pdf/acc/infosheets_pdf/G063.pdf "Who owns copyright in artistic works? An appropriate answer to a legal issue could have been: If Mick developed this administrative system as part of his work at BN College then the college owns the software and Mick is unable to implement the same system in a second location without the college’s permission. |
||||||||||||||||||||||||||||||||||||||
| END OF SECTION B | ||||||||||||||||||||||||||||||||||||||
Section CCASE STUDY |
||||||||||||||||||||||||||||||||||||||
Instructions for Section CAnswer all questions in the spaces provided. Remove the case study insert and read all the information provided before you answer these questions. Answers must apply to the case study. |
||||||||||||||||||||||||||||||||||||||
Flip Flop BakeryFlip Flop Bakery is owned by Sebastian, who is a baker. He employs two assistant bakers, three delivery drivers Flip Flop Bakery makes bread and bread rolls that it sells to the public through a shop. It also sells its bread, and a range of cakes and pastries that are bought from a wholesale cake supplier, to local restaurants, coffee lounges and clubs. A typical working day follows this sequence.
The problems Sebastian has identified a number of problems that, because of the growth of his business, have now become Proposed system To ensure the continued success of his business, Sebastian realises that he must make some changes to his ordering processes. Sebastian's daughter, Kayla, has just completed the first year of a university course in software engineering. She offers to look at how the problems might be solved.
Figure 1 |
||||||||||||||||||||||||||||||||||||||
Kayla knows that to help Sebastian she must first fully understand the problems, and then analyse the current system. To start her system analysis, Kayla has drawn the diagram (Figure 1) in the case study insert. It shows the movement of goods, invoices and orders associated with Flip Flop Bakery's operation, and the role of the various people involved. She now has to create a logical design for the bakery's information system by drawing a context diagram and data flow diagrams, as well as constructing a data dictionary. Question 1 Kayla has started the context diagram.
a. The label for the unnamed entity should be (1 mark) State average=0.5 Customer ... but where are the drivers? If bakers are external entities, why aren't drivers? Odd... b. Figure 1 in the case study insert shows three arrows going between the Cake supplier and the Bakery, but the context diagram only shows two. Explain this difference. 1 mark, 3 lines State average=0.2 Cakes are not data flow and should not appear in DFDs / context diagrams.. They are cakes. Yummy cakes. Is there a Cake Flow Diagram? c. Kayla has based her context diagram on Figure 1. Explain why she has drawn the Bakers as a separate entity. 1 mark, 3 lines State average=0.36 She's just wrong?? I have absolutely NO idea. Throw me a bone, someone. If bakers are external entities even though they exist within the data flow of Flip Flop Bakery, why are drivers not also external entities? Unless the drivers belong in the empty box in the question above... in which case why don't customers appear in the DFD? I'm confused. A reliable teacher friend says: 'They provide data to the 'system' rather than process the data so they would be considered entities rather the part of the system.' Ahhh. Everyone - remember that! The Bakers provide data to the system rather than processing the data, therefore they would be considered an entity rather than part of the system. |
||||||||||||||||||||||||||||||||||||||
Question 2
a. Identify the most correct data flow diagram. 1 mark State average=0.45 DFD C << official VCAA answer. I thought it was A. My approach was to find out what all 3 diagrams had in common so I could more easily discover where they differed. So the old highlighter came out. In red I marked all the items that all 3 diagrams shared. The remaining bits were marked in blue... Your strategy might have differed,
That helped me focus on the main points where the answer probably lurked. It became immediately obvious that in DFD B, its blue data flow had been discovered before: it was the 'cake flow', not a data flow. So that had to be wrong. In DFD A, the odd man out was "Ingredients getting low". That needed close checking. The case study insert definitely shows the bakers sending a list of ingredients that are getting low to Sebastian, so that looks fair enough. DFD C lacks this data flow - but then again there are several data flows missing in all 3 diagrams - invoices coming in from the bread ingredients supplier and cake supplier, and the outgoing orders for ingredients. Whether this was intentional or not is hard to see, but the question clearly asks for the most correct DFD... So DFD A seemed to be the most correct. A lot of brainwork for 1 mark. Ripoff! :-) But the thinking spent on 2a also supplies the answers for 2b, so it's not so bad... b. Explain the main error is in each of the other two data flow diagrams. 2 marks, 3.75 lines each State average=0.7 DFD B is incorrect because the input of "flours, yeast, sugar" is a flow of goods, not data. DFD C is incorrect because it lacks the "ingredients getting low" data flow from the bakers to 'Process Orders' DFD A is incorrect because it has an input ‘low ingredient’ that is not required to process orders. Also it does not lead to any output. Kayla has also created a data dictionary, part of which is shown below.
"Calculate quantities needed" is a process or algorithm, not a datum. It belongs in an IPO chart rather than in a data dictionary. Impress your friends at parties: say "a datum" at every opportunity. The inappropriate entry in the data dictionary was 'Calculate quantities needed' as this is a process, not an element of data. Kayla has completed her analysis of the system. She has decided to start the design of the new system with the design of the software. From her analysis she knows that one thing the system has to do is to calculate the required amount of each ingredient. She designs an algorithm that
The procedure will have passed to it data that lists the amount of each ingredient required for every bread item made by the bakery (Product_Recipes)
Question 3 It initialises all of the Qty array's elements to zero. It uses Ingredient_ID as the loop's index (counter). The REPEAT – UNTIL loop initialises (sets up) the array to store the quantity of each ingredient. To test the algorithm Kayla decides to use some simplified test data with only 1 bread product and only 3 ingredients. b. Using the data below complete the test table (3 marks) State average=0.3 Test data
That's odd. Why is the indexing of the array reversed? It should be (1,3) for example - product 1, ingredient 3. That's the order it is in the algorithm. (Note: this has been confirmed as a rare booboo by the SD exam writers. It's not significant to the answers, however.) Test table
c. Describe the error in this algorithm (1 mark) State average=0.1 The initialising of Ingredient_ID to 1 in line 12 is wrong because the variable is incremented at the start of the loop, so the starting value is actually 2, not 1. This makes it skip the first ingredient altogether. Ingredient_ID is set to 1 in the first of the nested repeat loops and immediately in the second part of the nested loop it is increased by 1, so the amount of the first ingredient is never calculated. d. Suggest one way the algorithm could be altered to fix this error (2 marks) State average=0.15 Ingredient_ID Either of: |
||||||||||||||||||||||||||||||||||||||
Question 4
This question type has occurred in a variety of forms since 2002; however, only a small percentage of students were able to gain full marks. |
||||||||||||||||||||||||||||||||||||||
Question 5 Data would be faster to access, modify, and manage. It would give functionality similar to a database. It would also be far easier to scale up to large sizes compared to a simple, dumb serial file. A record in a random file can be accessed instantly by its record number, and a record is read as a single cohesive package with a known structure. All the records between the current read position and target position can simply skipped over. Also, random file is opened for both read and write access. A serial file must be closed and reopened in the desired mode. A serial file must be completely read and written as a single unit. One can't (for example) open it, change data item 45 and close it again. You'd have to open it in read mode. Read all the data up to item 44 and simultaneously write it to a second file that is opened in write mode. You'd read the target item (#45), change it, write it to the output file, then go on and read every remaining data item and write it to the output file! That's a serious amount of disk activity to modify a single data element! Serial files are simply a sequential list of data items. To read an item from the list, one must start reading at the start of the file and read every data item up the one you want. If the data consists of groups of related fields (such as the buyer's name, the goods ordered and the quantity), you then have to read the items individually. If the reading gets 'out of sych' so you start reading data in the middle of a 'record' rather than at its beginning, you start getting rubbish data. The single-unit records in a random file, on the other hand, are read and written as a single object, and the fields in the records can be referred to easily by their field names. e.g. employee.surname (where employee is a record and surname is a field in the employee record.. Yeah - a bit longer than the 6 lines available on the paper, but I added more as an educational freebie. Appropriate responses included the following. |
||||||||||||||||||||||||||||||||||||||
STRUTH! THIS PAPER SEEMS TO GO ON FOREVER! |
||||||||||||||||||||||||||||||||||||||
Question 6 As part of the design of the new system, Kayla must decide what kind of mobile device the drivers should use.
State two advantages of each device for the given use. (6 marks, 2 lines each) State average=2.45 Note the bold words "given use". They don't want you talking about other activities the device could be used for. Laptop Advantage 1 - its keyboard is faster and easier to use for data entry Advantage 2 - its screen is far larger and can display much more data at once PDA Advantage 1 - data is transmitted - and can be acted on - as soon as it's received by the driver. There are no delays waiting for the drivers to return to the bakery before Sebastian can phone in his orders by the 3:00 deadline. Advantage 2- it's small, light and easy for the driver to carry in a pocket Others - Its battery would easily last an entire day's operation. Mobile phone Advantage 1 - like the PDA, data can be received from drivers before they return to base.* Advantage 2 - Its battery would easily last an entire day's operation.* * Try to avoid repeating the same answer for different sections, even if it's appropriate. Try thinking of something else. But it is hard trying to find an advantage of the phone that the PDA does not have.
|
||||||||||||||||||||||||||||||||||||||
Question 7
Recommended PDA - Strawberry Reason 1 - it has an internet enabled mobile phone which is necessary to send data back to the bakery (unlike the Watermelon's short-range Bluetooth) Reason 2 - the QWERTY keyboard will make data entry very convenient and quick. Also: the screen has good resolution and no other feature is significantly worse than the Peach.
|
||||||||||||||||||||||||||||||||||||||
Question 8
Refer to the beautifully mouse-drawn dependency arrows. Of course this Gantt assumes there are at least 2 programmers on the job! |
||||||||||||||||||||||||||||||||||||||
Question 9 Meaningful variable names make it easier to remember what variables are used for and help avoid using the wrong variable by mistake. Is is especially useful when you return to your code after some time has passed and you must re-learn your unintuitive names all over again. It is also valuable when other people must maintain your code. Internal documentation reminds the programmer and co-programmers what the code is meant to do and why things were done as they were. Without such inline documentation it is easy for you or a colleague to change some code without realising the implications of what you were doing. |
||||||||||||||||||||||||||||||||||||||
Question 10 a. A driver enters 100 dozen loaves instead of 1 dozen loaves. 1 mark. State average=0.4 A range check. b. A driver tries to enter an order for a bread product that Flip Flop Bakery does not make. 1 mark State average=0.5 An existence check (ensures selections exist in the bakery's catalogue) |
||||||||||||||||||||||||||||||||||||||
Question 11
a. What design error has she made? 1 mark State average=0.5 When deciding on the width of the interface, she has made it wider than the horizontal number of pixels the screen can display. b. How can it be improved? 1 mark State average=0.55 Reduce the font size of the labels and text boxes so they fit within the display's limits. Also move the buttons so they are fully visible. You know what you want to say, but it's hard to work out how to not sound dopey!
|
||||||||||||||||||||||||||||||||||||||
Question 12
a. What is the logical error with this screen? 1 mark State average=0.45 How can you tell whether you want to allow or cancel the message without knowing what the message is or whom it's from? b. Describe how to change this screen to correct this error. 1 mark State average=0.45 Add a control to display all or some of the message, or at least show the identity of its sender so you can judge whether you want to pay attention to it.
|
||||||||||||||||||||||||||||||||||||||
Question 13 a. State a concern with this training strategy other than the cost of shutting the bakery.1 mark State average=0.45 They are training everyone in everything, which means everyone will be getting some irrelevant information. b. Briefly describe a better approach to make certain that staff can operate the new system. 1 mark State average=0.55 People ought to be trained in groups according to their roles, so the content of the training can be tailored to their needs. |
||||||||||||||||||||||||||||||||||||||
Option 1 - Burn a video onto DVD so they can see what to do State which option is the best in this case and justify your answer. 4 marks 9 lines State average=2.45 Overall, Option 2. It depends a lot on how much information you want to give them. For very basic facts, the quick guide would suffice, and be very easily accessible. For comprehensive details, the website might be slow to access, but it can be quickly and easily updated. The help manual would take more time and skill to produce. Since they can't view a DVD on a PDA, option 1 is silly. Didn't like this question. It needed more context. Only 1 option was ridiculous: the other 3 had pros and cons but not enough is known about the amount of training the bakery wanted to give the drivers. |
||||||||||||||||||||||||||||||||||||||
Question 15
For each of these situations, explain a strategy that the bakery could use to limit or eliminate the concern. a. The website can be accessed by unauthorised people. 2 marks State average=1.25 Authenticate people accessing the site by making them enter a valid username and password.. b. There might be times when the PDAs are not able to connect to the web server. 2 marks State average=1.05 During times the PDA cannot connect to the server, the software should be able to store orders for later transmission when conditions are favourable. |
||||||||||||||||||||||||||||||||||||||
| Overall - a very challenging and very easy exam - in different places. Few complaints at all about quality of the expression or clarity of the questions. | ||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||
Back to the IT Lecture Notes index
Back to the last page you visited
Created 15 November 2007
Last changed: March 13, 2022 11:31 AM
Original Content © Mark Kelly 2007
Images and questions are © Victorian Curriculum
and Assessment Authority 2006. Reproduced here with permission for educational purposes.
VCE Applied Computing Notes © Mark Kelly