
Post Mortem Notes This is not a VCAA publication.
I do not speak for the VCAA, the IT examiners, or exam markers. I was not involved in the writing or marking of this examination. Extracts from exams are all Copyright © VCAA, and are used with permission. Use these post mortems at your own risk. I reserve the right to change my mind completely, at short notice, about anything I've said here. Suggestions, discussions and corrections are welcome. Questions look like this. |
||||||||||||||||||||||||||
|
Other VCE IT Exam Post Mortems to enjoy IPM / ITA / Informatics / Data Analytics - 2001 | 2002 | 2003 | 2004 | 2005 | 2006 | 2007 | 2008 | 2009 | 2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2023
|
||||||||||||||||||||||||||
Last changed: March 9, 2022 11:34 AM State average results added 16 December 2009 |
||||||||||||||||||||||||||
 |
The SMACKOS award is given to questions that are just plain WRONG: a complete dog's breakfast. |
|||||||||||||||||||||||||
 |
And a new coveted award: Questions That Make You Sick As A Dog.
or are wrong in a way that does not jeopardise the answer. |
|||||||||||||||||||||||||
NEW! I am proud to introduce an exciting new icon: the illiterate eye-chart to denote poor examination grammatical skills,
|
||||||||||||||||||||||||||
SECTION A - Multiple-choice questions
|
||||||||||||||||||||||||||
Instructions for Section A And let's hope this year's exam won't be a dog's breakfast...
|
||||||||||||||||||||||||||
Question 1
Joe and Helen have to name the database for their queen bee breeding program. The best filename from the list below is Answer is D. It's descriptive of its contents, unlike the alternative meaningless names. 90% of the state got this right. |
||||||||||||||||||||||||||
Question 2
The most appropriate user documentation to help students working in classrooms send their work to a networked colour printer in the school library is Answer is A. The manual is too detailed. The email is very inefficient and annoying. The reference card would need to be visible from any computer, which would be difficult. 81% of the state got this right. |
||||||||||||||||||||||||||
The Information Privacy Act 2000 applies to Victorian Answer is D. The Information Privacy Act 2000 only applies to public sector organisations, i.e. state government. The others are all in the private sector. 35% of the state got this right. |
||||||||||||||||||||||||||
Question 4
The design for a section of a spreadsheet shown above illustrates Answer is A. There is no testing visible; no functions are visible; validation is not apparent. Conventions include merging and centring text across columns; bold headings; centred headings; indication of units ($) in the heading. 73% of the state got this right. |
||||||||||||||||||||||||||
Question 5
The best design tool for representing the relationships between pages in the wiki on a website is a The official answer is C, but I think there is a case for B. A storyboard shows what pages/slides are in a site/slideshow/animation and how navigation occurs between them. Flowcharts design processes. 43% of the state got this right. |
||||||||||||||||||||||||||
Question 6
A milestone Answer is C. It is a diamond in a Gantt chart; B refers to a predecessor; D is hinting at slack. Milestones are points of progress and help project managers gauge whether they are running on time or not. Milestones have zero duration since they are not tasks that have to be carried out: they just happen. 67% of the state got this right. |
||||||||||||||||||||||||||
Use the following information to answer Questions 7—10. Sue uses the spreadsheet below to monitor her monthly income and expenses. 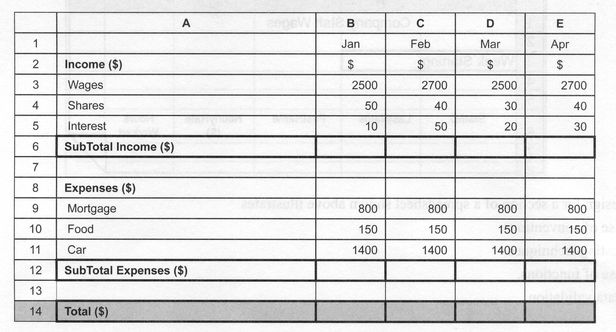 |
||||||||||||||||||||||||||
Question 7
The formula to calculate the SubTotal Income for January is Answer is C. It won't be A or B because they lack the equals sign that denotes that the cell contents should be interpreted as a formula (see grumpy note below). It can't be D because the formula would refer to itself, causing a circular reference error. Grumpy note: Are we now officially specifying Excel syntax as the only spreadsheet syntax in the world? Does every spreadsheet program in the world use the "=" to indicate a formula? Hmmm. Must check that out... 90% of the state got this right. |
||||||||||||||||||||||||||
Question 8 The Total amount of cash left to spend in February is most efficiently calculated in C14 by the formula Answer is B. Subtract total expenses (C12) from total income (C6). Not too hard... D would give the right answer but it recalculates values that have already been calculated, making it less efficient. Again, ruling out A because of the lack of an equals sign is a pedantic bit of frippery on the examiners' behalf, I believe. I like the word "frippery" 72% of the state got this right. |
||||||||||||||||||||||||||
Question 9
Typing the formula =IF(D12<D6,"HOORAY"," ") in D13 returns Answer is A. Using the data provided, D12 (total March income) is 1400+150+800 = $2350. D6 is 2500+30+20 = $2550. Plugging those figures into the formula gives
=IF(2350<2550,"HOORAY"," "). 70% of the state got this right. |
||||||||||||||||||||||||||
Question 10
Cell protection is most appropriate for all Column A and Answer is D. Cell protection is to prevent formulas being typed over. This question could confuse some students since in Excel you identify the cells that should be left unprotected, and then apply protection to the whole worksheet. The unprotected cells are available to be typed in, everything else is protected. This is slightly unintuitive and might cause some students to select the data cells (option B) as these are the cells they would actually nominate when applying cell protection in Excel. The students' response rate will be interesting to see when it's announced. 45% of the state got this right. |
||||||||||||||||||||||||||
Use the following information to answer Questions 11-13. Senior Secondary College uses database management software to organise the teacher and student use of printers. The relationships between the Student, Teacher and Print Job tables are represented below.
|
||||||||||||||||||||||||||
Question 11
In the one-to-many relationship between the Student table and the Print Job table Answer is A. Tricky one! Makes you stop and think... It's a one-to-many relationship (indicated by the 1 and infinity sign on the relationship arrow) which means the "one" end (student) can appear many times in the "many" end (print jobs). All of the options agree about that. That's not the issue. In the relationship, what is actually related? A record or a field within a record? A (key) field is used to identify a record, but it's the entire record that is related. So, one record in the print job table such as JobID: 12345 contains the field StudentID which allows the record of student ID S222 to be found in the Student Table from where his/her name, DOB fields etc can be retrieved. 38% of the state got this right. |
||||||||||||||||||||||||||
Below is a view of a section of the Student table.
|
||||||||||||||||||||||||||
Question 12
In this view of the Student table LastName is a Answer is B. 83% of the state got this right. |
||||||||||||||||||||||||||
Question 13
Using a value list or drop-down list for YearLevel is an effective validation technique because Answer is D. Effectiveness relates to how well the job is done: the quality of the finished product, including its accuracy. Reducing data entry errors is clearly an effectiveness measure. Ah - they got the name of a drop-down list right this year. Well done! 89% of the state got this right. |
||||||||||||||||||||||||||
Question 14
John has designed a spreadsheet to provide quotes for lawn mower repairs. Answer is C. It's the only one that relates to efficiency, which is concerned with saving time, money and/or labour. 69% of the state got this right. |
||||||||||||||||||||||||||
Question 15
Sam has to recommend a type of transmission media to support communication between two buildings 6 km apart. Answer is A. Bluetooth and infrared are very short distance (a couple of metres at best). CAT5e has a maximum length of 100m. That leaves only microwave. GRAMMAR ALERT: it should be 'a type of transmission medium'. Singular! Grammar takes a beating in this exam! And referring to CAT5e is so quaint. CAT6 has been the standard UTP cable for a long time now. And now we're heading to cat7! 44% of the state got this right. |
||||||||||||||||||||||||||
A dual prize-winning question! |
Question 16
Workers for a telephone help line use a computer system to key in details as each caller describes their problem. The computer provides a prioritised list of suggestions the worker can use to help the caller. Answer is D. GRAMMAR ALERT: Noun/pronoun agreement! It should be either "as each caller describes his or her problem" or "as callers describe their problems". Option A does not exist, as far as I know. Firstly, DSS is usually positioned in the tactical section of the organisational decision-making hierarchy. The case study is operational management as best, and probably not even management level at all. Secondly, if the computer is suggesting prioritised suggestions, it seems to be behaving as an expert system. Don't like this question. 60% of the state got this right. |
|||||||||||||||||||||||||
Question 17
A task performed by a network operating system (NOS) includes Answer is B. It's fairly damned obvious that a NOS is related to network matters. All the other options are purely workstation-based. 75% of the state got this right. |
||||||||||||||||||||||||||
 |
Question 18 A costume warehouse sells its 200 products on an online website and uses database management software to create tables for the stock. Two products are shown below.
Answer is B. In order: But it's ridiculous! A category table would only contain data about categories of items, not individual baseball caps - which is what a serial number describes! 68% of the state got this right. |
|||||||||||||||||||||||||
Question 19
The emergency plan within a disaster recovery strategy should include Answer is C. I very nearly gave this a Shmacko until I read the stem more carefully. It's referring to the emergency plan WITHIN a disaster recovery strategy. This section would describe what to do during the emergency. The rest of the document would describe what to do after the emergency when recovering from it. So we need to rule out "post emergency" actions such as reinstalling software (A, B) and supplier contact details (so you can get new copies of the software that was destroyed: option D.) The only option that only describes a plan of what to do during the emergency is C. But as one teacher pointed out: backups should be stored offsite. Evacuation should not be necessary! 42% of the state got this right. |
||||||||||||||||||||||||||
Question 20
Task X has 20 days duration and Task Y has 15 days duration. Task X is a predecessor of Task Y. Task Y cannot start until 10 days after Task X has finished. Answer is A. Fascinating! This is the first time I can remember the examiners going beyond really basic project management terms. I gloss over lag and lead times in class, just to be sure, but I sure don't stress them. I'd say this is one of those "A+" discriminator questions. Lag is the time a task must wait even though its predecessor has finished. Think of task X as "Pouring a concrete slab" and task Y as "Erecting the walls". Yes, task Y can't begin before task X ends, but it still can't start immediately: the cement must have time to cure. That is the 10 days' lag time. Lead time is the opposite. It can happen where a task theoretically has to wait for a predecessor to finish, but in practice a start can be made before the predecessor is completely finished. e.g. if emptying a computer room before rewiring the electrics, the sparkies could start work before every desk and computer were removed. As for options C and D, I haven't got the foggiest idea what they're about, so since I'm already happy with "lag", I'll ignore them. Since I have the luxury of Google, I looked them up and there were no hits for either term. The closest Google got was "When is the best time to start 'time out' with children?" GRAMMAR ALERT: it should be days' duration - the duration belongs to the days. 62% of the state got this right. |
||||||||||||||||||||||||||
Overall - few bad blunders by the examiners, but I really do not like 16. |
||||||||||||||||||||||||||
SECTION B - Short answer questions |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Answer all questions in the spaces provided. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 1 a. What is used to uniquely identify each record in a database? A key field. But it should be "table", not "database". Sloppy expression. Bad examiner. Bad! 1 mark State average for this question was 55% b. Backing up a database file by saving only data which has changed since the last backup is called Incremental backup. OR Differential backup. The examiners must accept either answer. The only (very pedantic and confusing) difference between incremental and differential is that a differential backup copies all changes since the last full backup, whereas an incremental backs up changes since the most recent backup of any variety. The terms are now usually used interchangeably. Anyway, since the question does not specify what sort the last backup was, I will be screaming quite loudly if 'differential' is not accepted! 1 mark State average for this question was 60% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 2
What a strange thing to announce. Some spreadsheets, sure, but this make it sound like it's compulsory in every spreadsheet! Complete the Input-Process-Output (IPO) chart to represent this action.
Too easy. 1 mark State average for this question was 45% b. Using the example: 6 items at $2.00 equals $12.00 i. what value(s) should be validated number of items, cost per item. ii. what value(s) should be tested? Total. This question is just finding out if you know that data (input) is validated for reasonableness (not accuracy) while calculations (output) are tested for accuracy. 1 + 1=2 marks State average for this question was 35% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 3 The Year 12 students at Country Secondary College have created a virtual private network (VPN) to organise the end-of-year barbecue. A committee of five students has decided to use an online chatroom where all Year 12 students can contribute to planning the location, music and food. a. Describe a security feature that will allow only current Year 12 students to read or join the chat. Login with username and password. Surely a VPN is way overkill for a stupid BBQ planning group? A simple web forum would suffice. 1 mark State average for this question was 65% b. The committee will use photos taken by parents of Year 12 students performing in the school's concert to promote the barbecue.
2 marks State average for this question was 68% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 4
\\coachserver\Reports\2009\Finance\X I wonder how lenient the markers will be. Not many kids, I think, will be familiar with the \\servername notation, and if students use forward slashes, will they be punished? 1 mark State average for this question was 50% Jack needs a new folder for netball photos used in this year's reports, b. Where on this diagram would you place this folder? i. Folder location Connected to the right of the SPORT shape. ii. Justify your answer. Photos belong in the images folder because they are neither reports nor emails. 1 + 1=2 marks State average for this question was 83% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
Jack has received a file called winners.doc to check. It is marked Read Only. He asks the Help Desk how he can add new text and send an edited file back to the coaches. c. List the steps the Help Desk should advise Jack to follow. 1. Open a file manager, locate the file, right-click it, select Properties, clear the "read only" box. 2. Open the file in a word processor, make his changes and save it again (preferably with a "version 2" added to the name) 3. Open his email program, attach the document to the email, address it to the coaches and send it. This was a bloody silly question. Three steps? To reset a read-only flag, add new text and send the file back comprises at least 12 steps to do it properly! 1. Reset the read only attribute. Can you imagine the screaming if the help desk actually gave just 3 steps? This unreasonably vague and silly question needed more thought and guidance for students. 3 marks State average for this question was 47% |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
d. The virtual team use an online application such as a wiki to write possible rule changes. GRAMMAR ALERT: The virtual team uses an online application. One team, collective noun - singular! Who's proof-reading these things anyway?? i. Describe how information is added to this online application. Contributors log in to the site hosting the wiki, and select the document to edit. They choose which part of the document they wish to edit, and they make their changes. Several users can edit a document simultaneously (but not the same part of the document [I believe - do different wiki programs behave differently?]) What else do the examiners want students to say? "It's typed in."? ii. Explain how the accuracy of the information is assured. It is proof-read by the people who make up the rules to ensure it's accurate, complete, relevant, unambiguous etc. It can be spell-checked. Hopefully, it's proof-read better than this exam has been. Spell-checking is often called 'validation', but I'm wondering if it really is. While spell checking sort of tests if a word exists in a limited list (of correctly spelled words in the dictionary), it does not check the reasonableness of the words (e.g. type, existence, range). But, then again, it does check input data but it's not testing the accuracy of a calculation. I'll ponder on this for a while... 1 + 1=2 marks State average for this question was 38% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 5 The VROOM racing car development team has drivers, pit crews and mechanics using a network to communicate during design and testing. Describe the function of each and identify a weakness, i. Firewall It monitors a computer's communication ports to detect and block unauthorised incoming and/or outgoing information transfers (e.g. port sniffing or transmissions by Trojans). It protects a computer against 'hackers.' Weakness
ii. Encryption Makes information unreadable to unauthorised people. Weakness
2 + 2 = 4 marks State average for this question was 49% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
Question 6 Jo uses a spreadsheet to manage customer data for selling downloaded music. CDs are mailed to customers who do not have an email address. 1 mark State average for this question was 60% It gives a realistic impression of the relative sizes, positions, colours, orientation of the finished screen without having to spend a lot of time actually creating it. Jo creates a macro to decide if customers receive an online download or are sent a CD in the mail. b. Recommend a design tool Jo can use to represent the IF statement in the macro. Justify your answer. Flowchart or Nassi-Shneiderman chart. Both charts are useful for designing processes and command flow such as that in an IF decision. 2 marks State average for this question was 15% - a shocking result for a disastrous question! This is a very strange one. Does Jo download the music and sell it, or do the customers download the music? If CDs are sent out, it means the customers are not downloading the music, but Jo is - which is probably a copyright violation. Fortunately, the absurd case study was completely irrelevant to the answer - the only thing that saved it from a SHMACKO. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 7 The owner of a new forensic laboratory will be responsible for many computer files used by the police. Each scientist's workstation will need physical, electronic and biometric security. Select one example from each type of security and describe how it protects the data and information on the workstation hard drive.
Physical example 1-Window bars Description 1 The bars physically deter people entering the room containing the workstations so the people cannot steal the computers (and the data) or damage the computers (rendering data unreadable). They also cannot get to the computer to log in and copy, delete or change data. Electronic example 1-User name Description 1 It requires a user to provide an ID that either identifies them personally (or, sometimes, as a member of a group). Without a correct usename the person cannot login to the network or computer. Usernames are invariably used with matching passwords because they're very weak security by themselves. Biometric example 1- Iris scan Description 1 The iris scanner captures an image of the pattern of the coloured part at the front of the eye. This pattern is unique. The pattern is digitally mapped to a simpler form and compared to the official recorded scans of authorised users. Only people authorised to access the data on the network or computer are given access to the data. Physical example 2-Padlocked processor case Description 2 A padlock secures the case's lid so the unauthorised people cannot reach into the case. This prevents unauthorised people removing and copying or stealing hard disks containing data, or shorting out the BIOS battery to remove the BIOS bootup password protection. Electronic example 2-Password Description 2 A secret code known only to a person who is authorised to access a computer, a network or a data file. It is usually used in conjunction with a corresponding username, and both the username and matching password must be given to gain access. Biometric example 2-Voice recognition Description 2 A person speaks into a microphone and their speech is analysed by software to detect distinctive features. These features are compared with authorised people's stored voiceprints. If voiceprints match, the person is given access. Voice recognition is a relatively unreliable form of biometric ID since voices are easily impersonated, and people's voices naturally change frequently due to their mood, health, breathlessness etc. 3 marks State average for this question was 82% A pretty simple question for a final exam, one would have thought. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 8
a. State a law which covers the car dealer's responsibility for this information. The Privacy Act (1988) Because the dealer turns over more than $3 million a year. For once the examiners have actually given basic, relevant info about the Privacy Act question so students can answer confidently! 1 mark State average for this question was 15% b. Describe a three-step procedure the car dealer must follow when collecting and storing this information. 1. Only collect data relevant to the transaction being carried out, or as required by law. 1 and a bit. Make sure the data is accurate, complete and up to date. 2. Not use a customer identifier that is used by another data holder. 2 and a bit. Take reasonable steps to protect the data against damage, loss or unauthorised access. 3. Make available a document that clearly sets out what information is collected and how it is used. I don't get it. A procedure is a structured series of actions to accomplish a task. It requires actions to be in order. Three steps (and only three) - in order? The question is fishing for Privacy Principle knowledge, I suppose, but how do get only 3 steps, and what order do they go in? Does offering a privacy statement come before or after taking reasonable steps to protect data from misuse?? Very odd. 3 marks State average for this question was 43% c. The registration and licence data is saved only to a flash disk. Recommend an efficient method for correctly disposing of electronic copies of this information. Justify your choice. Method: Hitting the flash disk with a very large iron hammer. If the examiners don't accept that, I'll be annoyed :-) Delete the files, wipe them with a disk-wiping utility, reformat the flash disk... then hit it with the aforementioned hammer. 2 marks State average for this question was 33% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 9 The screen shot shown below is a section of the home page of the Purity Water Company.
Layout and Relevance are two design elements to be evaluated in the website shown above. a. Describe how each of these design elements have been applied in this website. Layout Heading is bold and appears at the top. Explanations Bold headings clearly identify the content of the material below, making information easier to find. Highlighted navbar clearly identifies the text there are being different to other text in that it can be clicked. Aligning related items reinforces the fact that they belong together. White space allows items to be visually separated and made more distinct. It can also group related items (e.g. the four squares each have an icon, a bold heading, the "click for" text, then the description of the information that is linked to. Relevance All of the information on the screen is related to the products and services offered by the water company. e.g. The navbar links are the sorts of things people would expect to find on such a page. Explanation Irrelevant information wastes space and confuses people who must try to work out why it's there. Visitors want a site to deliver the information they expect to find there, and they expect to be able to find that information quickly and easily. 6 marks State average for this question was 46% b. Identify one audience characteristic that has been considered when producing this website. Explain how it has been considered. One characteristic is that visitors would be concerned about how to reduce their water consumption to help the environment. It has been considered by offering ideas and services to help them achieve this aim (e.g. how to reach a lower water usage target, and how to exchange their showerheads.) A terribly boring question. 2 marks State average for this question was 48% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 10 Sections of the Gantt and PERT charts used to monitor a project are shown below.
a. Draw in tasks Q R S and T and complete this section of the PERT chart.
4 marks State average for this question was 65% b. i. Identify the tasks on the critical path and its length. Tasks P,R,S,T Length 10 days ii. Identify the task with slack time and state the length of the slack time. Task Q Length 5 days The dummy task after Q is really necessary to finish the chart off neatly. It indicates a dependency with no actual work to do. In other words, the project cannot finish before Q finishes. 2 + 2 = 4 marks State average for this question was 54% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Question 11 UPod is an online company selling podcasts. The table below is used by UPod to keep track of its stock.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
Units in stock? What is this? Podcasts are electronic!
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
a. i. Which field could be used to locate the number of podcasts in stock? Duh - "Units in Stock"??? This question insults the intelligence of ITA students. ii. Which fields could be used to calculate the total value of podcasts in stock? Unit price, units in stock. 1+2 = 3 marks State average for this question was 85% b. Write a query or search rule to show the podcasts supplied by Bunny Podcasts. (Filemaker) In Find mode, type "Bunny Podcasts" into the supplier field and hit ENTER. 1 mark State average for this question was 30% Examiners: you have to accept that. It's how Filemaker does queries. It's not a scripted action. In a script one could enter Supplier = "Bunny Podcasts" but that's only one way to do it. c. The manager of UPod needs to know when stock gets to the reorder level. i. Write the rule for a query or search that returns a reorder alert message. IF(Units In Stock <= Reorder Level) Again, that's how a Filemaker script would do it (minus the action to take if the test is true) ii. Provide test data that sets off this reorder alert message. Product ID = 1 Units in stock = 20 Should trigger the alert. Note the alert should arise if quantity is EQUAL TO or less than the reorder level. The reorder level is the trigger. 1 + 1=2 marks State average for this question was 30% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
The table below stores details of UPod's Australian suppliers.
d. Hand draw an input form for UPod to add a new Australian supplier to the table shown. The company standard font is Arial size 14. Background colour is grey.
State average for this question was 40% It's a bit vague what they wanted: just a drawing or a proper mockup with formatting information shown as well. They really should give students a bit more guidance. I added the extra information just to be on the safe side. When Sam's fifteen-year-old brother Gino ordered a podcast from UPod, UGambling sent him the following email.
e. Identify an ethical dilemma for the management of UPod and UGambling raised by this email. i. UPod management Should we profit by providing contact information to Ugambling if we don’t know the age of our customers?
ii. UGambling management We may be sending promotional gambling material to children or gambling addicts who might be badly affected or influenced by the material. iii. Write a question you would ask the management of UGambling about sending this email to a teenager. Do you know that the recipient was a child below the legal age to gamble and what effects this email might have had on him? How did you get this child's email address? 1 + 1 + 1=3 marks State average for this question was 55%
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
The section of the Delivery Costs spreadsheet below shows the delivery cost and weight of each item to be delivered to customers.
Costs are calculated by the weight of each item using the following rates. 1 to 20 kg is $10 a. Write the most efficient formula to calculate delivery cost in cell D6 that can be replicated or dragged down cells D7 to D9. Where range F8:G11 is named 'TABLE'... =VLOOKUP(C6,TABLE,2) 1 mark State average for this question was 15% None of this $F$8:$G$11 rubbish! |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
As Bobby has pointed out, the examiners have once again (e.g. 2007 question B11) screwed up a VLOOKUP question. If you check the lookup table, it's just wrong. It would need to look like this to return the desired values...
And no - nested IF is never a good idea! |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Late goof alert
|
4 November 2010 - a wise little bird has pointed out that the examiner's report gave this answer: =VLOOKUP(C6, $F$8:$G$10,2) or =VLOOKUP(C6, F$8:G$10,2) Obviously the formula was supposed to refer to G11, not G10. Quite ironic that the examiners complained about the students having difficulty writing formulas! |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
b. The manager needs an alert in the worksheet if the Total Weight of all items in a delivery is greater than 900 kilograms. i. Write a formula for an alert. =IF(C12>900,"ALERT - TOTAL WEIGHT IS OVER 900kg!", " " ) A bit repetitive. We've done this sort of IF thing earlier... twice. In A9 and B11c(i). This is the third time! ii. Recommend a cell where you would place an effective alert. D12 Justify your answer. It's right next to the piece of data that is causing the alert, thereby indicating the cause of the alert. iii. Provide one value of test data in an appropriate cell that would trigger your alert.
1 +(1 + 1)+ 1 =4 marks State average for this question was 50% Again - test data has already been examined in B11c(ii). Are they running out of key knowledge to test?? The manager has designed the worksheet below to keep track of the delivery statistics.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
c. Write the reference formula that places the correct value for Total Weight in the DeliveryStats worksheet. =TOTALWEIGHT (where cell C12 on the DeliveryCost sheet has been named 'TOTALWEIGHT') They want me to use that stupid sheet!cell format. Well, I refuse! I never EVER use worksheet names in references. It's ugly and stupid and unnecessary. If the examiners refuse to accept my answer, again I'll be kicking VCAA heads from here to Footscray. 1 mark State average for this question was 10% |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
d. The warehouse has kept statistics of petrol used each month. i. Describe how this information should be presented in a yearly report. A pie chart. ii. Justify your answer. It would clearly show the annual usage of petrol by month making it clearer which months contributed most to the cost. I guess the examiners would and should also accept bar charts, line charts or even a table as long as it was reasonbly justified. 1 + 1=2 marks State average for this question was 43% |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
The manager has designed a new delivery slip for each customer. The slip for Mrs Wright shown below uses data from the worksheet Delivery Cost and another worksheet called Customer Info.
e. i. Recommend an efficient procedure to automatically create a delivery slip for each customer. Firstly, stop using a bloody spreadsheet! Export the data to a a database with an output form that can neatly lay out each customer's data. This is really starting to annoy me. Are they trying to get students to say MAIL MERGE or something equally silly? Only newbies use spreadsheets to produce individualised documents like delivery slips or cheques. See below if you want to join in the fun and try to create the spreadsheet described above. ii. Justify your answer. Because using mail merge is inefficient, and spreadsheets really SUCK at producing individualised mass output. The whole idea of doing this in a spreadsheet is ludicrous. I refuse to go on because this is getting too silly. 1 + 1=2 marks State average for this question was 33% Ah, thank dog I got that off my chest! This question was originally awarded a Sick Dog Award, but I've upgraded it to a SHMACKO for its implied advocation of a ridiculously inappropriate IT technique. If the examiners' report proves they had some other technique in mind, I will retract the SHMACKO... But for the life of me I can't think of any other method except for mailmerge. END OF QUESTION AND ANSWER BOOK |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
It's amazing! B12 has earned two Shmackos and a Sick Dog Award all by itself! |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
OverallToo easy. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
I am not impressed. Why - year after year - do such ignorant and vague/confusing questions still appear on the ITA exam? Something needs to be done about it. It's embarrassing to all of us who try to seriously promote ITA as a respectable VCE study. 1. Hire someone who can construct a sentence in proper English. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
 |
Play the B12 spreadsheet game!Fun for the whole familyThe challenge is to create the delivery docket spreadsheet exactly as described in the ITA exam question B12e without using mail merge!And since the question says for you to "automatically create a delivery slip for each customer", Best of luck. A spreadsheet starting point is available for anyone who wants to play. It's the best I could manage. Ignore it if you prefer. |
|
Back to the IT Lecture Notes index
Back to the last page you visited
Created 11 November 2009
Last changed: March 9, 2022 11:34 AM
VCE Applied Computing Notes © Mark Kelly 2001-
Original Content © Mark Kelly 2009
Images and questions © Victorian Curriculum
and Assessment Authority 2009. Reproduced here with permission.